Leadership & Management
Knowing what is happening in the marketplace is vital to the success of your enterprise
Read More
How Dependence Can Ruin A Supply Chain
The economic horizon was showing signs of new life and your business-improving Orders were up, but you have concerns that you have stretched the length of your supply chain
February 1, 2014
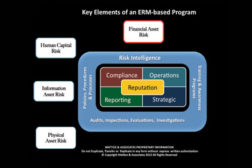
Understanding and Mitigating Financial Asset Risk
How is Cybercrime the new Wild West of Theft?
November 5, 2013
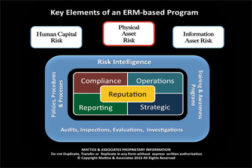
How to Manage Physical Asset Risk
Our journey on the road to transforming to an Enterprise Risk Management based program, one of the more traditional security sweet spots, is our next area of focus.
October 1, 2013
How to Safeguard Your Information Assets
How are lapses in cyber security leading to the loss of billions of dollars worth of intellectual property?
September 1, 2013
Understanding People, Your Enterprise’s Top Asset and Risk
Singing Kumbayah won’t keep insider threats away.
August 1, 2013
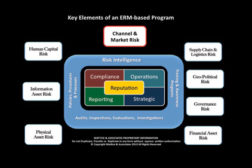
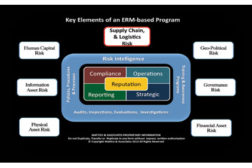
Why Risk Intelligence is the Key to Successful Security
Risk intelligence is one of the most important of the core elements which must be established when building a successful and effective enterprise risk management program.
July 1, 2013
Keep Security Current with Audits, Analysis and Updates
Previously in this series we have addressed leading by understanding and embracing ERM.
June 1, 2013
Communicate, Communicate, Communicate
Nothing is more basic than effectively communicating.
May 8, 2013
Sign-up to receive top management & result-driven techniques in the industry.
Join over 20,000+ industry leaders who receive our premium content.
SIGN UP TODAY!Copyright ©2024. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing