- NEWS
- MANAGEMENT
- PHYSICAL
- CYBER
- BLOG
- COLUMNS
- EXCLUSIVES
- SECTORS
- Arenas / Stadiums / Leagues / Entertainment
- Banking/Finance/Insurance
- Construction, Real Estate, Property Management
- Education: K-12
- Education: University
- Government: Federal, State and Local
- Hospitality & Casinos
- Hospitals & Medical Centers
- Infrastructure:Electric,Gas & Water
- Ports: Sea, Land, & Air
- Retail/Restaurants/Convenience
- Transportation/Logistics/Supply Chain/Distribution/ Warehousing
- EVENTS
- MEDIA
- MORE
- EMAG
- SIGN UP!
Home » security risk management
Articles Tagged with ''security risk management''
Security 500: How Security’s Risk Mitigation Focus Creates a Risk-Nado!
What are the Top 10 Trends enterprise security executives concerned with now, and what should you plan for in 2014?
November 5, 2013
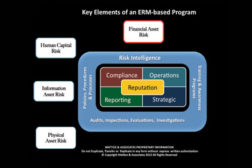
Understanding and Mitigating Financial Asset Risk
How is Cybercrime the new Wild West of Theft?
November 5, 2013
How to Plan for Post-Incident “Golden Minutes”
You've heard about the "Golden Hour" after an incident, but you should be planning for the "Golden Minutes."
November 5, 2013
Is Your Program Security Theater?
Is your department making the enterprise safer, or is it a false sense of security? Take our quiz to find out!
September 1, 2013
How Access Control Fits into Multi-Tenant Housing Security Budgets
While video gets all the press, access control can be the key to incident prevention in housing facilities.
September 1, 2013
Sign-up to receive top management & result-driven techniques in the industry.
Join over 20,000+ industry leaders who receive our premium content.
SIGN UP TODAY!Copyright ©2025. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing