Articles by Lynn Mattice
Are enterprises in an impossible situation when it comes to dealing with insider threats?
Read More
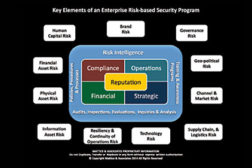
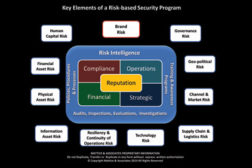
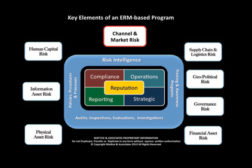
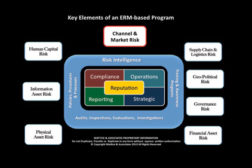
Managing Risk Across the Enterprise
The key to the risk-based security program is that no matter what issue you examine, every one of them affects the reputation of the enterprise in one manner or another.
July 1, 2014
Controlling Brand Risk
How the market perceives a company and its brand(s) ultimately dictates success or failure.
June 1, 2014
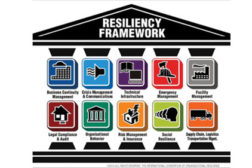
How to Add Resiliency to Your Risk Management Strategy
The latest buzzword these days is “Resiliency,” which for all intents and purposes is really nothing more than a new term for business continuity planning (BCP) in the private sector and continuity of operations planning (COP) in the public sector.
May 1, 2014
How to Keep Up with Emerging Technologies and Risks
consumers hundreds of billions of dollars annually. In the United States, credit card fraud resulting from cyber intrusions has skyrocketed.
April 1, 2014
Earning Security Success by Monitoring the Marketplace
Knowing what is happening in the marketplace is vital to the success of your enterprise
March 1, 2014
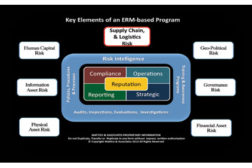
How Dependence Can Ruin A Supply Chain
The economic horizon was showing signs of new life and your business-improving Orders were up, but you have concerns that you have stretched the length of your supply chain
February 1, 2014
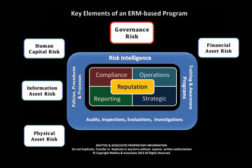
How to Keep Up With Governance Risk
Establishing and maintaining a culture across the enterprise that is based on unwavering ethical practices from the boardroom to the lowest level employee is also a key element of effective governance programs.
December 1, 2013
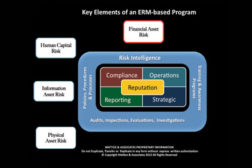
Understanding and Mitigating Financial Asset Risk
How is Cybercrime the new Wild West of Theft?
November 5, 2013
Debating the NSA, Espionage and Hackers with Congressman Mike Rogers
A Frank Look at the World Today with Congressman Mike Rogers
October 1, 2013
Sign-up to receive top management & result-driven techniques in the industry.
Join over 20,000+ industry leaders who receive our premium content.
SIGN UP TODAY!Copyright ©2024. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing