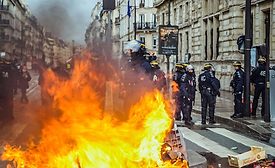- NEWS
- MANAGEMENT
- PHYSICAL
- CYBER
- BLOG
- COLUMNS
- EXCLUSIVES
- SECTORS
- Arenas / Stadiums / Leagues / Entertainment
- Banking/Finance/Insurance
- Construction, Real Estate, Property Management
- Education: K-12
- Education: University
- Government: Federal, State and Local
- Hospitality & Casinos
- Hospitals & Medical Centers
- Infrastructure:Electric,Gas & Water
- Ports: Sea, Land, & Air
- Retail/Restaurants/Convenience
- Transportation/Logistics/Supply Chain/Distribution/ Warehousing
- EVENTS
- MEDIA
- MORE
- EMAG
- SIGN UP!
Featured on Home Page
Planning for the unplanned: How organizations can build their resilience to protests and other unplanned events
Here are five crucial steps your organization can take to ensure business continuity and resilience to protests and other unplanned events.
November 11, 2020
Three video surveillance tools for SMBs
Small-to-medium-sized businesses have a number of unique considerations when it comes to video surveillance.
November 9, 2020
Security 500 Thought Leader Profiles
Leo Simonovich: Thriving in a Digitized Environment
November 5, 2020
Security 500 Thought Leader Profiles
Kevin Wilkes: Securing the Arts
Chief Security Officer
November 5, 2020
Sign-up to receive top management & result-driven techniques in the industry.
Join over 20,000+ industry leaders who receive our premium content.
SIGN UP TODAY!Copyright ©2025. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing