Columns
The disclosures by Edward Snowden over the past year have raised the public’s awareness about the U.S. Government’s surveillance tactics and capabilities to defend our nation against another 9/11 magnitude attack.
Read More
5 Common Mistakes in Cyber Incident Response
Network intrusions have become a fact of corporate life, and increasingly are viewed as among the many costs of doing business.
August 1, 2014
Why America Needs a CSO
The loss of intellectual property due to theft by China costs the U.S. more than $300 billion annually and translated into 2.1 million fewer jobs in this country.
August 1, 2014
7 Free Cybersecurity Planning Resources for SMEs
Cybersecurity is now a primary concern of senior executives within both the Fortune 500 and, perhaps more importantly, the “SME 28.”
July 1, 2014
5 "Hot Spots" for Business Travel Security
Determining the “hot spots” and travel trends for 2014 and beyond requires a reflection on past years.
July 1, 2014
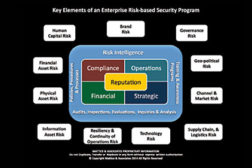
Managing Risk Across the Enterprise
The key to the risk-based security program is that no matter what issue you examine, every one of them affects the reputation of the enterprise in one manner or another.
July 1, 2014
Why Customized Cybersecurity Training is Essential
If you asked your employees to define “cybersecurity,” what would they say?
July 1, 2014
Enterprise Benefits from the Security 500
The Security 500 Benchmark Program is your tool to enter your security-related data and receive a confidential and free benchmarking report.
July 1, 2014
Lessons Learned from Security 500 Palo Alto
How little opex can you spend and still get the job done
June 1, 2014
Using Security Convergence to Enable the Enterprise
Enterprises realize tremendous benefits from this convergence as well as some serious downsides, but the trend is irreversible.
June 1, 2014
Sign-up to receive top management & result-driven techniques in the industry.
Join over 20,000+ industry leaders who receive our premium content.
SIGN UP TODAY!Copyright ©2024. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing