Security Talk Column
Small business doesn’t necessarily mean small data.
Read More
Securing Schools After Sandy Hook
Last year, on December 14, 20-year-old Adam Lanza fatally shot 20 young children and six adults at Sandy Hook Elementary School in Newtown, Ct.
December 1, 2013
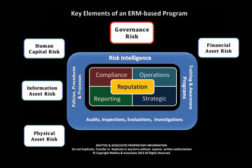
How to Keep Up With Governance Risk
Establishing and maintaining a culture across the enterprise that is based on unwavering ethical practices from the boardroom to the lowest level employee is also a key element of effective governance programs.
December 1, 2013
Studying the 'Wicked Problem' of Cyber Security
Cyber crime has been referred to as a “wicked problem,” and its solution may well lie in stronger education.
November 5, 2013
10 Ways to Secure Enterprise Data Over the Holiday Season
As we all soon will head out on upcoming holiday vacations, we all run the danger of becoming a remote risk for our companies, often without being aware of it.
October 1, 2013
The Good Old Days of Cyber Security
Advanced Persistent Threats (APTs) are proving traditional cyber attacks (viruses, malware, etc) outdated, according to Larry Clinton, President & CEO of the Internet Security Alliance.
September 1, 2013
Leading Security at 1,700 Feet
How does Keith Kambic manage security for the Willis Tower, the tallest building in Chicago?
August 1, 2013
Strengthening Passwords with the FIDO Alliance
The average consumer has 35 passwords, but how secure are they?
June 1, 2013
Understanding the DIY Security Trend
When know-how information, or knowledge, is scarce, customers overcome it by doing it themselves.
May 9, 2013
How Cyber Security Changes Leadership Skills
Kieran Norton believes that cyber security is undergoing an important change.
May 9, 2013
Sign-up to receive top management & result-driven techniques in the industry.
Join over 20,000+ industry leaders who receive our premium content.
SIGN UP TODAY!Copyright ©2024. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing