Cybersecurity News
Special Report
2021 Top Cybersecurity Leaders - Roy E. Hadley Jr.
Special Counsel, Adams and Reese LLP
February 1, 2021
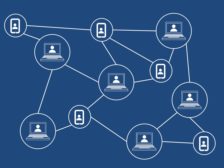
How two-factor authentication works with blockchain
In this article, we discuss how two-factor authentication has been evolved to address the shortcoming of single authentication systems. We also discuss how we can utilize a blockchain technology to transform 2FA by migrating the centralized network into a decentralized blockchain network. As more Internet-of-Things devices require authentication credentials and users increase their repository of usernames and passwords for accessing web services, the emergence of 2FA solutions based on blockchain technology is inevitable.
February 1, 2021
Sign-up to receive top management & result-driven techniques in the industry.
Join over 20,000+ industry leaders who receive our premium content.
SIGN UP TODAY!Copyright ©2025. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing