Security Leadership and Management
Atlanta’s Operation Shield Video Integration Center (VIC) started with a mere 17 city-funded cameras three years ago.
Read More
The Future of DHS Partnerships with Frank Taylor
In its recent Quadrennial Homeland Security Review, the Department of Homeland Security outlined its strategies for becoming a more integrated and agile agency
August 1, 2014
Extending Dignity and Respect to Security Officer Contracts
Virtually every company will have a statement of some kind extolling the senior leadership’s commitment to treating people with dignity and respect.
August 1, 2014
Why America Needs a CSO
The loss of intellectual property due to theft by China costs the U.S. more than $300 billion annually and translated into 2.1 million fewer jobs in this country.
August 1, 2014
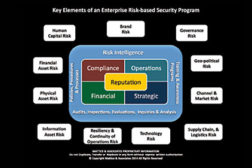
Managing Risk Across the Enterprise
The key to the risk-based security program is that no matter what issue you examine, every one of them affects the reputation of the enterprise in one manner or another.
July 1, 2014
Enterprise Benefits from the Security 500
The Security 500 Benchmark Program is your tool to enter your security-related data and receive a confidential and free benchmarking report.
July 1, 2014
Sign-up to receive top management & result-driven techniques in the industry.
Join over 20,000+ industry leaders who receive our premium content.
SIGN UP TODAY!Copyright ©2024. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing