Security Leadership and Management
Managing Risk Across the Enterprise
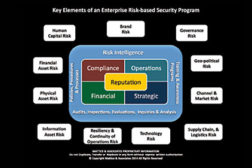
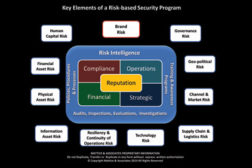
The key to the risk-based security program is that no matter what issue you examine, every one of them affects the reputation of the enterprise in one manner or another.
July 1, 2014
Enterprise Benefits from the Security 500
The Security 500 Benchmark Program is your tool to enter your security-related data and receive a confidential and free benchmarking report.
July 1, 2014
2014 Security Leadership Issue: Building Security's Brand for Better Buy-in
In a wired world that is also full of risk, an enterprise’s reputation can be destroyed in hours.
June 1, 2014
Lessons Learned from Security 500 Palo Alto
How little opex can you spend and still get the job done
June 1, 2014
Controlling Brand Risk
How the market perceives a company and its brand(s) ultimately dictates success or failure.
June 1, 2014
Why the Security Talent Gap Is the Next Big Crisis
The next national security crisis may be a lack of ability to mitigate or respond to such an attack because frankly, there’s no one available to mitigate the attack or respond to it.
May 1, 2014
Finding Sustainability's Purpose in Security
The most environmentally sustainable building in the world is the Change Initiative Building in Dubai, based on the LEED Commercial Interiors rating system.
May 1, 2014
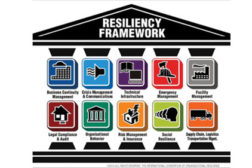
How to Add Resiliency to Your Risk Management Strategy
The latest buzzword these days is “Resiliency,” which for all intents and purposes is really nothing more than a new term for business continuity planning (BCP) in the private sector and continuity of operations planning (COP) in the public sector.
May 1, 2014
Sign-up to receive top management & result-driven techniques in the industry.
Join over 20,000+ industry leaders who receive our premium content.
SIGN UP TODAY!Copyright ©2024. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing