AlertEnterprise Guardian Predict™
AlertEnterprise delivers powerful next generation Physical Identity and Access Management software for corporate and critical infrastructure protection. Additionally, with Guardian Predict, AlertEnterprise combines machine learning and predictive risk analytics to detect behavior anomalies and deviation from regular access patterns. Safeguard against Insider Threat by tracking when employees or contractors enter critical areas outside their normal shift hours, or without a corresponding work order.
The combined categories of employees, contractors, vendors and visitors that have been granted access to the organization at any given instant in time make up the badged population. It is important for security managers to know how large the badged population is, what risks they pose to the enterprise and how to mitigate the risk.
Identity Intelligence software can rely on machine learning and the deployment of rules. For example, John Q is a control room worker who has been following a steady shift pattern of working Monday through Friday, nine to five. He suddenly starts showing up at midnight on a Saturday and uses his work badge to access a secure area. The deviation from the pattern of nine to five on weekdays and the exception to the rules that people with John’s role should not be accessing a room that stores the critical assets sets off a series of alerts to various stakeholders including security personnel.
Tracking Non-Standard Behavior (NSB) delivers additional value-added capabilities like monitoring for insider threat, badge utilization, repeatedly violation of rules, and space utilization are all excellent reasons to deploy Identity Intelligence.
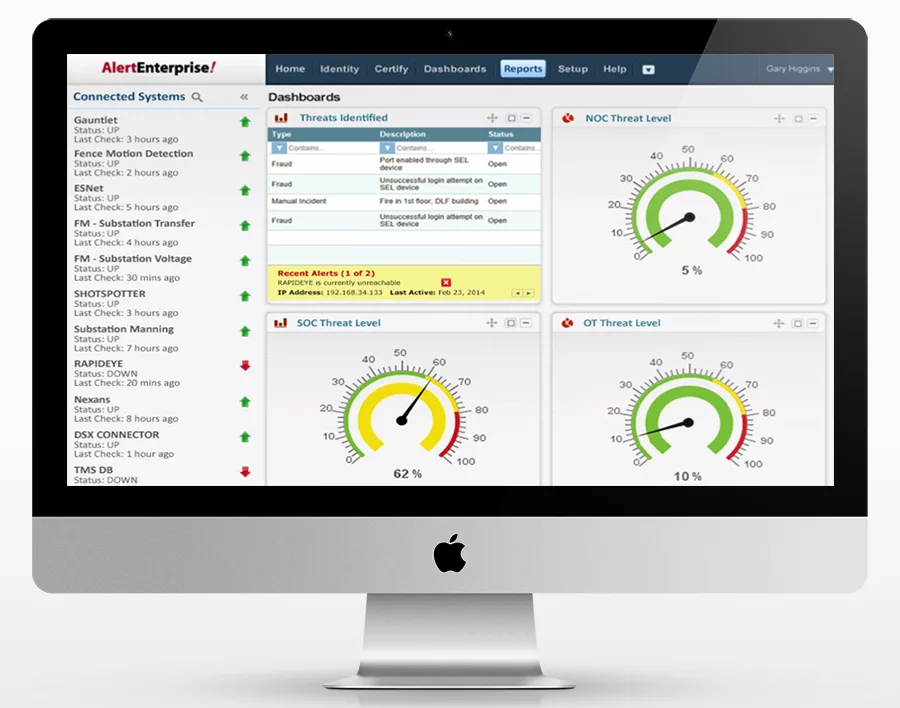
Purpose-built Risk Analytics and Risk Management features provide capabilities not available in traditional badging solutions. AlertEnterprise can leverage user attributes, access patterns, and policy violations to calculate risk scores for individual users. Our solution automatically detects anomalies and sends alerts on exceptions. Combined with customizable reports and dashboards, and a dynamic reports designer, enterprises can leverage this capability to address hard-to-find insider threat vectors and indicators of compromise. Key capabilities include:
- Risk Scoring – attributes
- Access Behavior Monitoring - Anomaly Detection
- High Risk Individual Accessing High Risk area
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!





