Metrics Justify IP Transition
The “table” referred to, of course, is where top executive managers of companies meet to discuss the business of increasing marketshare, growing revenues, returning value to shareholders and beating the competition. More and more, the talk at this table includes risk management and the strategy to protect the corporate brand from the negative impact of security breeches and compliance violations.
So what does it take for CSOs, CISOs and corporate security directors to get a seat at this strategic table? And why do some companies make a seat at the table for the security executive while others are left standing at the door? These questions are crucial as security operations move more decisively to IP-based security video and access controls for both physical and logical security needs.
Companies that include security executives in strategy and risk management discussions have three things in common:
- Security executives more skilled at defining the business case for investment in security technology and services, and able to position security as a competitive differentiator.
- A security organization with more extensive and meaningful relationships with their business partners at all levels throughout the company.
- Security executives who better measure security value using metrics to justify spending and resources to sustain a secure and compliant enterprise.
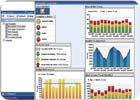
Metrics measurements help security get a seat at the corporate table. Click image for larger view.
Combining elements
Few companies can deny that security is essential to competing in their markets. For example, headline-grabbing security breeches, for example, have proven to be a reason that customers change from one bank to another or avoid a healthcare or retail business. This creates an opportunity for security executives to demonstrate how security enables the business by protecting physical and information assets. Management reporting and metrics can put security information into the context of business success. This also balances the cost of security against the revenue produced by the business transactions.Security effectiveness is a combination of technology, process and people.
Top security professionals share one characteristic: They are very good at collaborating with business partners to create and enforce policy that doesn’t restrict an agile business. Collaboration requires communication -- the ability to listen and understand their business counterparts and the ability of security to affordably automate the generation of metrics that can assure their partners that security is working.
Often security relies on highly visible catastrophes, perceived threats and regulatory mandates to justify spending. But metrics, displayed on a security dashboard, provide the concise, practical and highly visual summaries to justify additional spending. Collecting, analyzing operational statistics and turning them into action oriented, strategic metrics that business executives can understand requires automation.
For example, Khalid Kark, senior analyst for Forrester Research, an independent technology and market research company, writes in a 2006 research paper, “Are We Secure Yet?,” that “most (security professionals) realize that they can no longer keep asking for increasing budgets or using the excuses that they don’t have time to measure security or that measuring security is simply impossible.”
In a recent survey, sponsored by this author’s company, Intellitactics, and conducted and analyzed by Frost and Sullivan, security executives surveyed reported they are starting to use metrics or are planning to use metrics to measure security value. Specifically, almost half, or 46 percent, have already begun using metrics to measure security value, with about 43 percent planning to take an action in the coming year. About 60 percent of those taking steps to measure security performance are doing so to justify spending. In addition to justifying spending, the other strategic reasons cited for using metrics to measure security performance include an interest in improving security process, measuring the impact of security on business availability and the interest in providing regular communication to management. In both the Forrester research and the Intellitactics/Frost survey, the top areas for measuring and monitoring were regulatory compliance and incident handling and response. V
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!



